Blog > Sage Intacct Payment Processing Security: PCI-DSS Compliance Guide
Sage Intacct Payment Processing Security: PCI-DSS Compliance Guide
For organizations that rely on Sage Intacct, how payments move through the system has a direct impact on financial accuracy, customer trust, and overall risk exposure. You already know how busy day‑to‑day operations can be—managing invoices, closing books, handling audits—so the last thing your team needs is a preventable security or compliance issue tied to payment data.
This guide walks through what PCI‑DSS really means in a Sage Intacct environment and how to build secure, compliant workflows. Whether you’ve been using Sage Intacct ERP for years or you’re just beginning to integrate payment tools, this is designed to give you grounded, practical guidance—without the jargon.
Understanding Why PCI‑DSS Matters in Sage Intacct
Payment Card Industry Data Security Standards (PCI‑DSS) exists to protect cardholder data anywhere it’s stored, processed, or transmitted. If your organization accepts credit card payments of any kind, you fall under PCI requirements. And when payments run through Sage Intacct payment processing, those responsibilities continue—whether you’re accepting recurring donations, customer payments, fee-based services, or anything else.
Non‑compliance isn’t just a technical issue. It can lead to fines, forensic audits, reputational damage, or—in the worst cases—long‑term financial consequences. For finance teams already stretched thin, that’s not a situation you want to face.
When credit card data touches your systems, logging, transmitting, or storing, PCI-DSS applies. The same goes for Sage Intacct credit card processing, whether it’s handled through native tools or a connected payment processor.
How Sage Intacct Helps Support PCI‑DSS Compliance
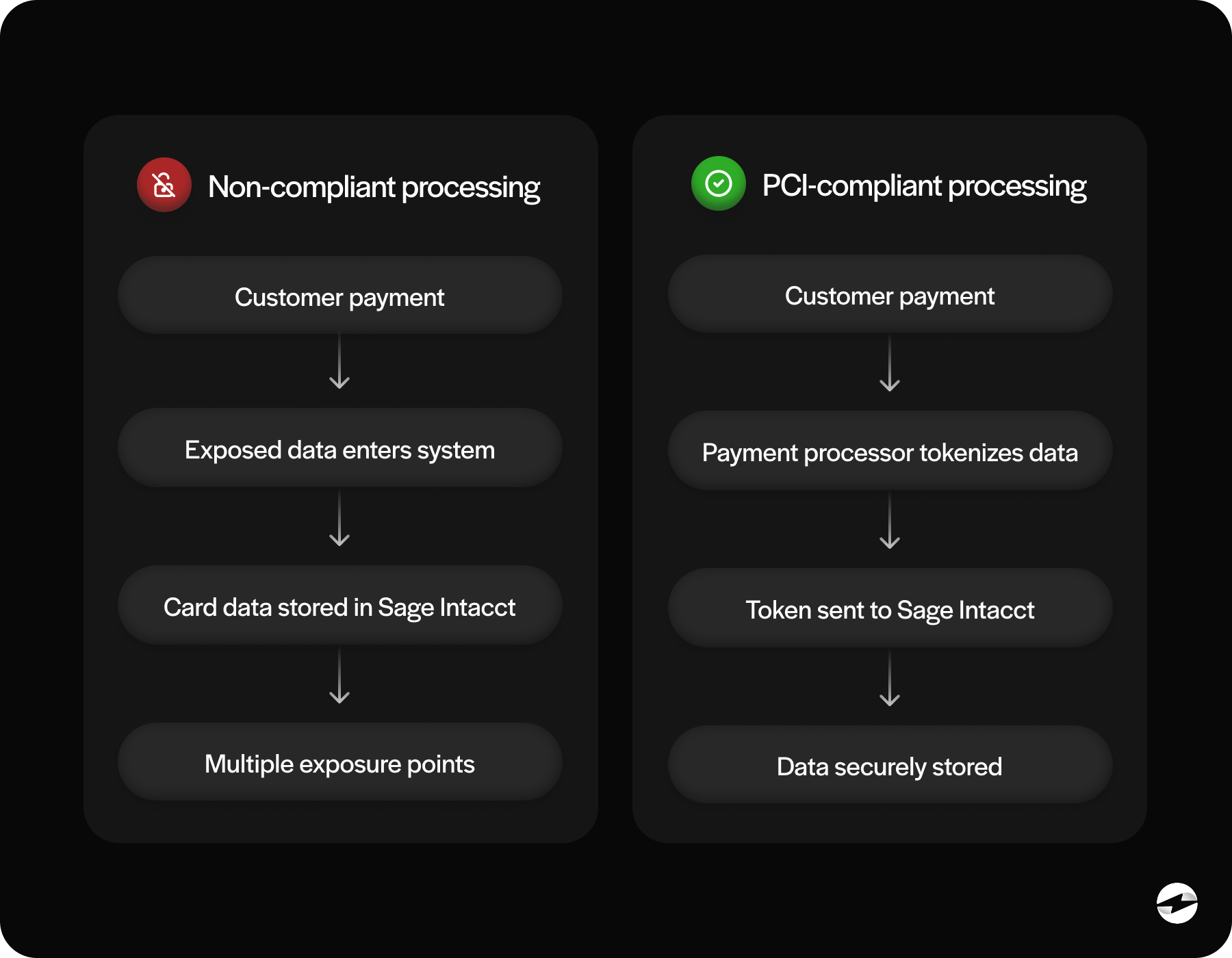
The good news is that Sage Intacct software includes strong foundational protections. Its structure is built around limited data exposure, controlled access, and secure communication. Sensitive cardholder information is never meant to be stored directly in Sage Intacct, and its design reinforces that.
Through tokenization, encryption, and secure communication channels, Sage Intacct payment processing reduces how much sensitive data your organization touches in the first place. When integrated with a PCI‑compliant payment processing solution, Intacct becomes part of a broader security ecosystem that prevents raw card data from entering your internal environment.
It’s also worth noting that avoiding common Sage Intacct integration mistakes—like unsecured API calls or unvetted third‑party add‑ons—strengthens your PCI posture considerably.
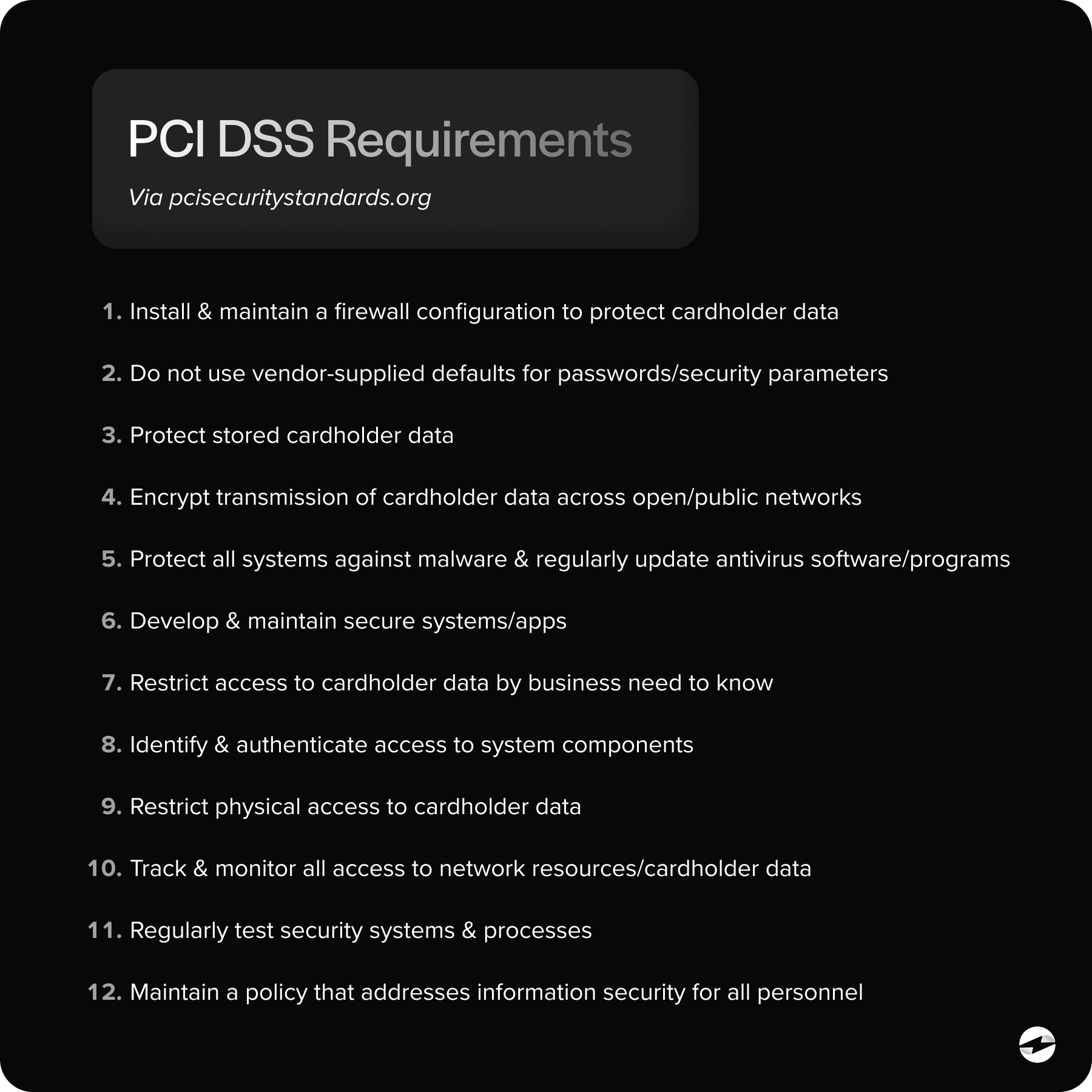
Breaking Down PCI‑DSS Requirements for Sage Intacct Users
PCI‑DSS can be overwhelming at first glance, especially if you’re more accustomed to accounting or operational workflows than security frameworks. But you don’t need to become a security engineer to follow the basics.
For Sage Intacct users, PCI often comes down to:
Minimizing access – Only people who need to interact with payment functions should have permissions. This limits exposure and reduces error.
Securing integrations – Any system connected to Sage Intacct must move data securely. This includes CRMs, donor platforms, and every payment processor.
Avoiding storage of raw card data – Sage Intacct isn’t built to store sensitive credit card information. Tokenization replaces raw numbers with safe, unusable substitutes.
Maintaining audit trails – Logs, user history, and transaction trails help meet PCI requirements and simplify audits.
When you look at the requirements through the lens of everyday Sage Intacct usage, they become far more manageable.
Securing Sage Intacct Integrations and API Connections
Many organizations underestimate how much of their PCI compliance depends on their integrations. A system can be secure on its own, but once you connect additional tools—and most businesses do—the level of risk shifts.
The Sage Intacct API is powerful, but it must be used responsibly. Every endpoint, every data transfer, and every sync is part of your PCI footprint. Poorly written or outdated integrations can leak data, mishandle authentication, or expose sensitive information.
A strong Sage Intacct integration partner will design API connections that enforce encryption, tokenization, and secure credential handling. They’ll also ensure that no credit card data ever enters Sage Intacct in a raw form. Cutting this corner is one of the most common integration mistakes—and one of the most preventable.
Best Practices for Protecting Cardholder Data in Sage Intacct
Protecting cardholder information isn’t just about meeting PCI standards—it’s about reducing risk for your team and your customers. You don’t want staff manually typing card numbers or handling data in ways that create unnecessary exposure.
Some practical best practices include:
Use a PCI‑compliant payment processor. This reduces your PCI scope dramatically.
Rely on tokenization. Tokens replace card numbers, protecting sensitive data in your internal systems.
Limit user permissions. Not everyone needs access to payment modules.
Conduct routine audits. Even small changes can create exposure if they affect integrations or payment workflows.
Automate wherever possible. The less your team manually touches card data, the more secure your processes become.
Each of these steps supports the integrity of Sage Intacct payment processing and reduces the chance of accidental exposure.
Auditing and Monitoring Inside Sage Intacct
Monitoring payment activity is one of the strongest defenses you have. Sage Intacct ERP offers flexible audit trails that track user actions, posting history, and changes in real‑time. For PCI compliance, this makes a meaningful difference.
Regular review of these logs helps you catch unusual activity early—incorrect permissions, unexpected integrations, or suspicious behavior. Many teams are surprised how often small anomalies, left unnoticed, lead to larger security risks.
Internal controls, approval workflows, and recurring review cycles make your PCI posture more resilient, especially in environments with multiple departments entering or reconciling payment data.
Choosing a Secure Third‑Party Payment Processor
Not all processors offer the same level of security, and your choice directly impacts your PCI requirements. A secure payment processing solution should provide encrypted transactions, tokenization, and seamless integration into Sage Intacct payment processing.
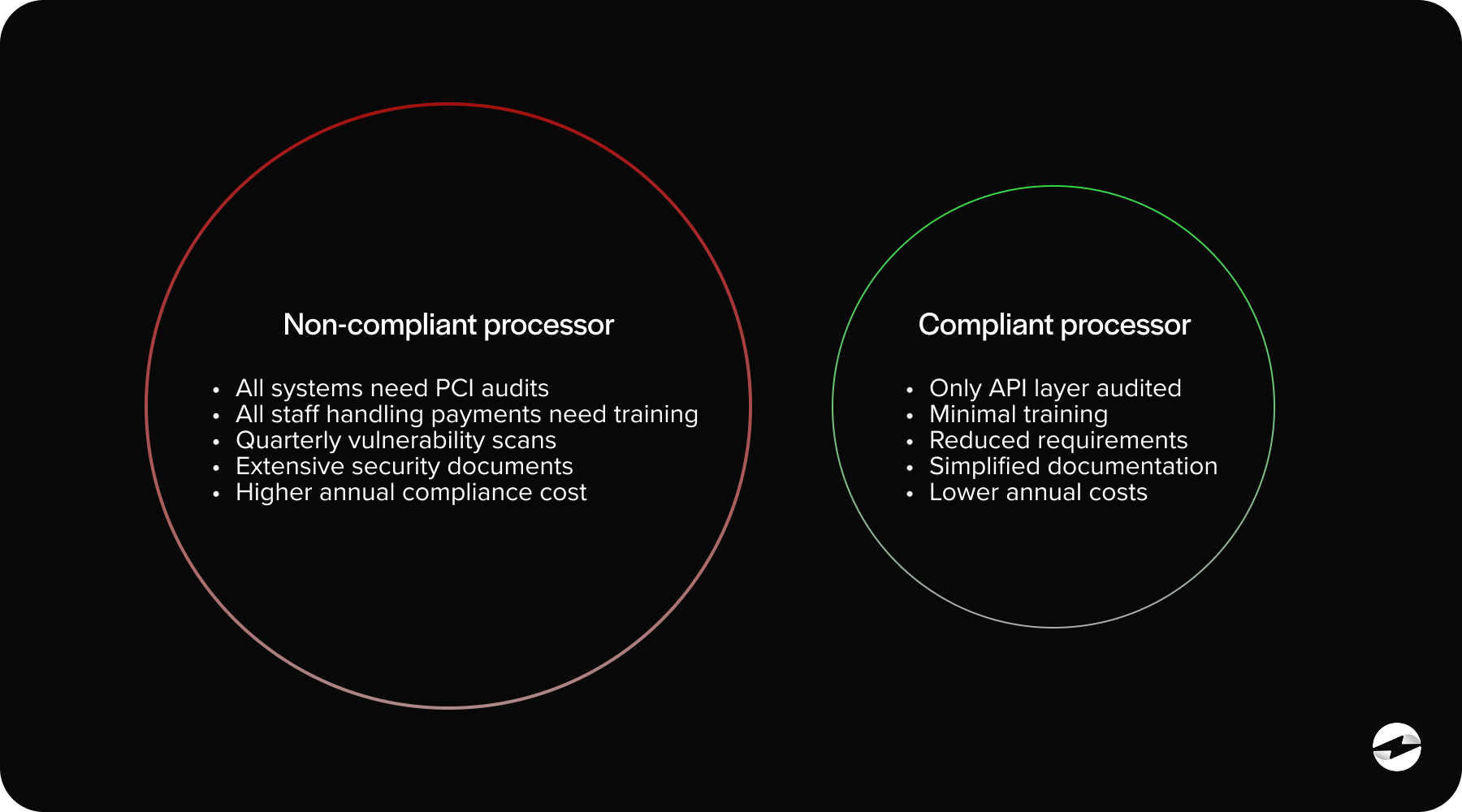
This is where the right partner becomes critical. A strong payment processor protects your team from ever handling vulnerable data and reduces your compliance burden by keeping the most sensitive steps outside your environment.
A trusted provider also helps you avoid common Sage Intacct payment integration mistakes, like sending card data through unsecured channels or relying on unsupported custom scripts.
Why EBizCharge Helps Strengthen Long‑Term Compliance
PCI compliance isn’t a “set it and forget it” type of deal. Standards evolve, cyber threats change, and payment workflows shift. A reliable partner adapts alongside those changes.
EBizCharge is a strong match for organizations using Sage Intacct because its security model is built around encryption, tokenization, and secure data handling. Its native Sage Intacct integration means card data never enters Sage Intacct in a raw format. Instead, it’s captured, tokenized, and secured entirely through the payment processor before syncing securely through the API.
This significantly reduces the PCI scope your internal systems must manage.
EBizCharge also updates its compliance protocols proactively, aligning with new PCI requirements as they emerge. For finance teams juggling reconciliations, closing cycles, and audits, this level of built‑in protection removes a major burden.
Maintaining Compliance Over Time
Any time you add a new integration, modify your workflows, or update your Sage Intacct environment, your PCI obligations shift, too.
Maintaining compliance means:
- Reviewing integrations annually.
- Validating that your payment processor still meets all PCI requirements.
- Keeping user permissions up to date.
- Ensuring your Sage Intacct API connections continue to use secure methods.
A partner like EBizCharge supports these ongoing needs by minimizing your exposure and keeping security processes current without putting extra work on your team.
Building a Secure, Compliant Sage Intacct Payment Environment
Secure payment processing isn’t optional—it’s part of protecting your organization, your customers, and your financial data. With Sage Intacct ERP, PCI‑compliant workflows, and the right integration strategy, you can create a highly secure environment without complicating everyday operations.
When you combine strong security practices with a reliable Sage Intacct integration partner and a PCI‑focused payment processor like EBizCharge, you’re not just meeting compliance standards—you’re building a safer, more efficient financial system for your team.
Staying compliant becomes easier, data stays protected, and your payment workflows run smoothly from end to end.
- Understanding Why PCI‑DSS Matters in Sage Intacct
- How Sage Intacct Helps Support PCI‑DSS Compliance
- Breaking Down PCI‑DSS Requirements for Sage Intacct Users
- Securing Sage Intacct Integrations and API Connections
- Best Practices for Protecting Cardholder Data in Sage Intacct
- Auditing and Monitoring Inside Sage Intacct
- Choosing a Secure Third‑Party Payment Processor
- Why EBizCharge Helps Strengthen Long‑Term Compliance
- Maintaining Compliance Over Time
- Building a Secure, Compliant Sage Intacct Payment Environment