Blog > How To Prevent Data Breaches: 15 Best Practices
How To Prevent Data Breaches: 15 Best Practices
Now more than ever, businesses are focusing on preventing data breaches and implementing response protocols to mitigate breaches if they occur.
According to the 2023 IBM Data Breach Report, the global average cost of data breaches was $4.45 million this year, up 15% over the last three years.
To effectively implement preventive solutions, businesses need to understand what data breaches are and familiarize themselves with their most common causes.
What are data breaches?
Data breaches occur when unauthorized users gain access to sensitive or confidential information, such as personal data, financial records, or trade secrets. These breaches can have devastating consequences, both financially and in terms of reputation.
An incident is only considered a data breach if the confidentiality of data is compromised. Sensitive or confidential data can include customer data records, bank account numbers, Social Security numbers, healthcare information, intellectual property, etc.
Threat actors employ various methods and techniques to execute data breaches. Malware attacks, such as ransomware and viruses, infect systems through malicious software or email attachments. Phishing attacks trick individuals into disclosing their login credentials or other sensitive information through deceptive emails or websites. Weak passwords and social engineering attacks also contribute to unauthorized access. According to Verizon’s 2023 Data Breach Investigations Report, 74% of all breaches involve a human element, whether it’s due to error, misuse of privileges, the use of stolen credentials, or through social engineering.
By implementing the most reliable security software and best practices, organizations and individuals can mitigate the risk of data breaches and safeguard their valuable information from malicious actors.
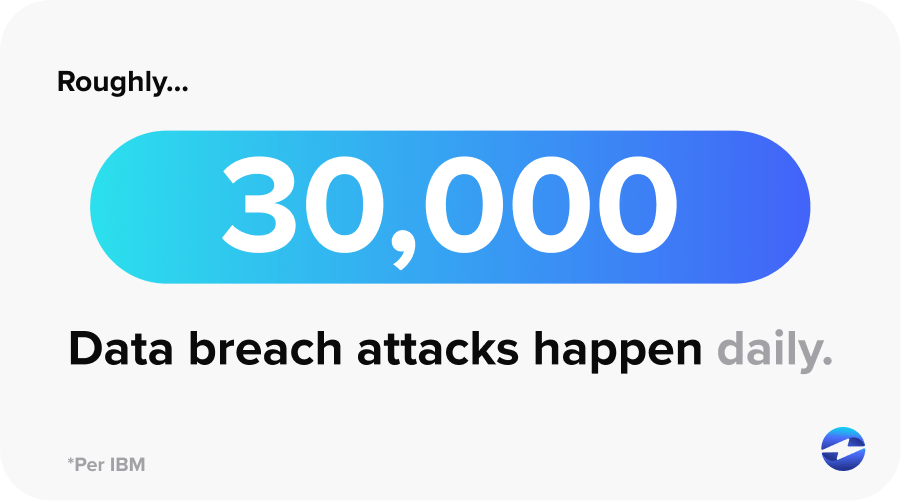
With roughly 30,000 data breach attacks happening daily, these threats may seem unavoidable. Thankfully, businesses can review common data breach causes to prevent them in the future.
Data breach examples
While there are various causes for data breaches, they typically all share the same goal of accessing and stealing sensitive information.
Nonetheless, the four most common data breach causes are social engineering, stolen physical information, human error, and unsecured networks and systems.
1. Social engineering
Social engineering can occur when attackers gain access to a system or network by convincing users to provide credentials. Phishing attacks are the most common way to get these credentials, but other methods can be used to access this information.
Ultimately, psychological manipulation is used to trick individuals into giving away sensitive information or making security mistakes.
2. Stolen physical information
Physical information can be stolen when a malicious actor gains access to sensitive information found in documents, devices, or hardware.
For example, the Heartland Payment Systems suffered a physical breach in 2015. Thieves stole confidential computer equipment and gained access to payroll, Social Security, and banking information. This incident cost the company $140 million in damages, fees, and penalties.
Another common cause of data breaches is social engineering.
3. Human error
Human error is one of the leading causes of data breaches in organizations since internal staff can and do make mistakes. Employees handling sensitive information may inadvertently divulge this data or share their credentials.
Therefore, it’s essential for all staff, regardless of department and data exposure, to go through the proper training to detect phishing attacks or other breach attempts.
Despite the many causes of data breaches, companies can implement several practices and protocols to prevent and avoid data breaches altogether.
4. Unsecured Networks and Systems
Companies with unsecured networks and out-of-date systems are at a higher risk of data breaches.
Therefore, businesses must secure their networks and systems to prevent unauthorized access by deploying strong encryption, setting up firewalls, ensuring accurate user authentication processes, and more.
It’s also essential for your team to regularly monitor networks for suspicious activity or potential vulnerabilities.
How to prevent data breaches
Since data breaches can cause significant damage, businesses must be diligent and proactive to prevent, address, mitigate, and avoid these threats.
To help with this, here are 15 best practices for your company to implement to prevent data breaches:
- Continuously create and update procedures
- Secure data disposal
- Data encryption
- Backup and recovery strategy
- Only store essential data
- Stay educated and understand the threat landscape
- Protect your company’s physical information
- Employee training and awareness
- Maintain up-to-date security software
- Remote and routine monitoring
- Monitor your company’s portable devices
- Phishing prevention
- Collaborating with cybersecurity experts
- Firewalls and intrusion detection systems
- Employee exit protocols
1. Continuously create and update procedures
Staying up to date on cyber security and ever-evolving threats is just one piece of the puzzle. Using this knowledge to create and update your procedures to address new threats is essential.
Creating and updating procedures ensures that employees know and follow the most up-to-date security protocols. Regular training and communication can reinforce the importance of cybersecurity and provide employees with the knowledge and tools they need to protect sensitive data.
By staying vigilant and proactive, businesses can minimize vulnerabilities and effectively safeguard against breaches.
2. Secure data disposal
When you have data you no longer need, it’s essential to dispose of it using secure methods.
Secure data disposal consists of physical document shredding, wiping or sanitizing devices using special software to make data unrecoverable or unreadable, and physically destroying devices to render them unusable.
Businesses must enforce safe and reliable policies to securely dispose of different data.
3. Data encryption
A 2020 PANscan found that 88% of merchants stored unencrypted data on their network consisting of exposed credit card numbers, which is a clear violation of PCI compliance.
To prevent such breaches, businesses must encrypt data to ensure that it remains indecipherable even in the event of a breach.
4. Backup and recovery strategy
Developing a backup and recovery strategy allows your business to quickly respond to an emergency or disaster.
To ensure the successful execution of your data recovery plan, all important operational data should be saved on another protected system, and daily system backups should be conducted.
5. Only store essential data
The more information you collect and store, the greater the risk of severe damage if a breach occurs. Prioritizing essential data storage can reduce risks and minimize damages should a breach occur.
Conduct data audits periodically to determine which data is essential. Assess each type of data and consider whether it is necessary. If not, then stop collecting it.
6. Stay educated and understand the threat landscape
The world of cyber security is constantly evolving. Today’s strategies and methods to prevent data breaches may be less effective in a year or two.
Staying educated on the threat landscape will help you stay on top of advancements and changes to best practices.
7. Protect your company’s physical information
Physical information is still vulnerable to theft and unauthorized access. So, companies must implement the proper protocols to protect this information.
Your business can physically protect its data by storing devices in secure and inaccessible places, limiting and monitoring access to devices that contain sensitive data, and investing in building security to prevent unauthorized entry.
8. Employee training and awareness
If you want to know how to prevent a security breach, the first step is to train employees. Every employee accessing the company’s network or devices increases the odds of a security breach.
Therefore, businesses should conduct onboarding, including security training and routine training on updated security best practices. Training your employees raises awareness of security risks and bad habits that can lead to a successful cyber attack.
9. Maintain up-to-date security software
While security software works to prevent attacks, this effort can be undone if a security hole allows hackers to access your network. Data breaches will likely occur if an organization fails to maintain strict security measures and update its policies to evolving threats.
To better secure your network and business, keep security software and any additional software updated with the most recent safety measures and tools in place.
10. Remote and routine monitoring
Since data breaches can occur at any time, businesses must be vigilant and continuously monitor their systems.
Your company can continuously monitor its systems and networks by constantly observing, analyzing, and recording to identify and address security vulnerabilities in real time.
11. Monitor your company’s portable devices
Bringing your own device (BYOD) and portable device issuance pose a significant risk, so companies must track these devices to protect against data breaches.
By proactively monitoring portable devices, you can guarantee that data is encrypted, devices are password-protected and secure, and anti-theft software is installed. If portable devices are stolen or easily accessible, an imminent data breach can occur.
12. Phishing prevention
When looking at the 2023 FBI Internet Crime Report, about 43% of the total complaint counts (excluding Cryptocurrency and Crypto wallets) are due to phishing/spoofing, as it remains the most common method of cybercrime. In the year 2022, the reported losses or resulting financial impact from phishing/spoofing attacks was a costly $160,015,411. Thankfully, employee training and education can prevent most phishing attempts.
For the best prevention, onboarding and retraining protocols should include information on identifying fraudulent phishing emails and other attempts. Your business can also install malware scanners to monitor their email systems for potential phishing threats.
13. Collaborating with cybersecurity experts
While learning the various data breach prevention methods can be daunting, business owners can collaborate with cybersecurity experts for additional help.
Cybersecurity experts can assist in preventing data breaches by running network penetration tests, identifying security risks, deploying patches and fixes, and creating security protocols.
If data breach prevention fails, you can rely on these experts to work alongside your IT team to prevent further damage.
14. Firewalls and intrusion detection systems
Security experts are taught how to prevent security breach incidents using strict firewall rules and intrusion detection systems. Software and hardware firewalls should be in place to stop unwanted traffic from accessing your network.
Firewalls can also filter outbound traffic to prevent employees from accessing malicious websites.
Advanced intrusion detection systems will work behind the scenes to monitor your network and identify threats and unwanted network traffic.
15. Enforce secure offboarding protocols
Only 29% of organizations enforce a formal offboarding process, making it one of the most overlooked methods to avoid data breaches.
Offboarding protocols should include recovering company assets and devices, updating access controls and permissions, and securing company documents and data.
With proper offboarding and employee exit procedures, businesses can receive helpful feedback and opportunities to prevent future breaches.
How to deal with security breaches
While implementing best security practices can protect and prepare your business against breaches, no strategy is foolproof.
Resolving a data breach is often lengthy and time-sensitive, so creating a plan can help. Should a data breach occur, here are five steps your company can take:
- Act quickly
- Assess the scope of the breach
- Notify and engage IT and security teams
- Immediately alert all parties involved
- Identify and fix vulnerabilities
Act quickly
In 2022, businesses took 277 days to identify and contain data breaches, which can be detrimental to your success and customer base.
If a data breach occurs, companies must have procedures to quickly respond to attacks and work with IT professionals to prevent further damage.
Next, your team should assess the scope of the breach.
Assess the scope of the breach
Assessing the scope of the breach is a time-intensive process. You’ll need to understand the content of the breach.
What data was encrypted and breached? What data was unencrypted? Were encryption keys taken? What is the worst-case scenario for the attack? All these questions must be answered.
After assessing the scope of the breach, your company should meet with security professionals.
Notify and engage IT and security teams
Businesses should consult with their IT and security teams to better understand the data hackers accessed, how they gained access, and what steps to take.
Enforcing strict security measures can enhance your data breach protection, allowing you to deploy patches and address security gaps.
While it may be a difficult conversation, alerting all parties affected by the breach is essential.
Immediately alert all parties involved
When addressing and resolving a data breach, it’s important to alert all parties involved and other relevant parties.
You likely need to report the breach to law enforcement, business partners, investors, affected businesses and customers, and anyone who may have had their data exposed.
Identify and fix vulnerabilities
In addition to resolving current threats, security and IT teams should continuously work to prevent data breaches from recurring.
Part of the breach resolution process may include the help of third-party security professionals to isolate specific devices to learn how the attack occurred and what can be done to mitigate future breaches.
Businesses can take immediate measures to prevent unwanted network traffic and halt the worsening of a breach. After identifying and fixing any security vulnerabilities, you can restore network functionality.
The key is to apply a thorough data breach resolution plan, prevention strategies, and security tools to secure your business.
How to avoid security breaches
It’s essential to prevent data breach incidents to reduce the risk of losing customers, tarnishing your brand reputation, and facing fines and penalties.
While these tips and tools are a great starting point, businesses should regularly review their infrastructure and operations, stay up-to-date on the latest security trends and threats, and work with cybersecurity experts to ensure long-term success.
 Is you business PCI compliant? Take this 1-min quiz to find out.
Is you business PCI compliant? Take this 1-min quiz to find out. 

