Blog > 3 Steps to Ace the TLS 1.2 Upgrade
3 Steps to Ace the TLS 1.2 Upgrade
In 2015, the PCI Security Standards Council announced changes to its security standards that have reverberated across the payment landscape: merchants are no longer allowed to use SSL or TLS 1.0 to secure credit card information. Merchants have until June 30, 2018, to migrate and upgrade to TLS 1.2.
What are SSL and TLS?
You may have seen the terms SSL and TLS floating around on the internet, but what do they mean?
SSL (Secure Socket Layer) was developed in the 1990s as a protocol to protect online communications from outside forces. For example, when someone bought a book from Amazon, SSL protected their credit card information as it traveled across the internet. For many years, SSL was an essential tool in the web security arsenal.

Why is TLS vulnerable?
Because TLS is the most common protocol to protect information online, it’s susceptible to attacks from those seeking to steal data. Known attacks (like BEAST, CRIME, POODLE, and Heartbleed) have impacted TLS 1.0 and essentially made it useless, allowing attackers to harvest sensitive data. Unfortunately, it’s impossible to patch or fix these vulnerabilities, so merchants must migrate to TLS 1.2.

What’s the deal with TLS 1.1?
You may have noticed that there are three versions of TLS: 1.0, 1.1, and 1.2. While TLS 1.1 is more secure than TLS 1.0, it’s still not the safest option for merchants and their customers. To avoid costly data breaches and all their attendant effects, merchants should implement TLS 1.2.

What happens if I don’t upgrade to TLS 1.2?
If you don’t upgrade to TLS 1.2, you’re putting your business and your customers in very real danger. If a data breach occurred due to known vulnerabilities in TLS, your business could face penalties from the PCI Security Standards Council for being non-compliant, including fines ranging from $5,000 to $100,000. Your bank could choose to end your relationship, effectively barring you from processing credit cards. And of course, you’d lose the trust and respect of your customers and take a hit to your reputation.
Putting data breaches aside, if you don’t upgrade to TLS 1.2 by June 30, then it’s likely that you won’t be able to process payments. Many payment gateways are proactively making the switch to TLS 1.2 and encouraging their clients to do the same. If you don’t take responsibility for your end, then you might wind up on July 1, 2018, unable to process credit cards.

How can I implement the TLS 1.2 upgrade?
The deadline for implementing TLS 1.2 is fast approaching, so it’s best to get started now. Here are three steps to help you make the switch:

1. Do some research
Before you make any changes, it’s important to do your research and verify whether your systems need to be upgraded or not.
If you use payment terminals or POS devices, you may or may not be required to upgrade them to TLS 1.2. Certain terminals use SSL and TLS 1.0 but may not be vulnerable to known attacks, so contact your terminal vendor to determine if your terminals are safe from attacks. Once your vendor verifies your terminals, you must use up-to-date patches and disable any unnecessary extensions. If your terminals are already using TLS 1.2, then you won’t have to take any extra steps.
Ever since the upgrade was announced, payment gateways have been working toward migrating all their merchants to TLS 1.2. If you use a payment gateway, then you’ve probably already received information about the upgrade. As you prepare for the upgrade, double check with your payment gateway to determine if you need to take any steps on your end to upgrade your servers, browsers, or operating systems.
Likewise, eCommerce stores have been working toward creating TLS 1.2-compatible platforms. eCommerce stores are especially vulnerable to SSL/TLS attacks, so if you use an online store, it’s imperative that you make sure it’s safe. As with your payment gateway, your eCommerce store should’ve already contacted you about the change, so check in with them about any steps you need to take.
Take heed: if you don’t make sure your payment gateway and/or eCommerce store are compliant with TLS 1.2, then you won’t be able to process payments on July 1, 2018.
Once you’ve done your research, you can move on to creating a comprehensive migration plan.

2. Create a migration plan
If you’re going through a PCI DSS assessment process, then you’ll need a formal migration plan in place. If not, then a migration plan will still give you guidance while you upgrade to TLS 1.2. Think of it as a roadmap—a document that covers every aspect of the transition.
The first stop on your roadmap is auditing your current environment and determining what needs to change. Your processing environment—which encompasses everything from your payment gateway to your servers to your web browser to your eCommerce store to your POS terminals to your web hosting provider and more—must be compliant with TLS 1.2, so it’s important to be thorough.
If you’re feeling lost, here are some questions to consider when creating your migration plan:
- How are you currently using old/vulnerable protocols? (TLS 1.0 and SSL)
- Do they serve any purpose in your business? Can you abandon them?
- Before you make the migration, do you have any risk reduction controls in place? What are they?
- How are you monitoring for new vulnerabilities?
- How will you make sure that your new systems/environments won’t use old protocols?
- What are your goals and how do they fit into the timeline for migrating by June 30, 2018?
For more in-depth information, this PDF from the PCI Security Standards Council covers everything you need to know about migration plans. (NB: This document says the deadline for migration is June 30, 2016, but the deadline has since been moved to June 30, 2018.)
When your migration plan is in place, you’ll be ready to make the upgrade.

3. Make the upgrade
Making the upgrade to TLS 1.2 should be handled by your IT or security professional. (If you don’t have an army of security professionals at your beck and call, don’t worry. The PCI Security Standards Council recommends that small business owners contact their acquiring bank to ensure their environment meets all requirements for upgrading to TLS 1.2.)
Here are a few tips from the PCI Security Standards Council on how to successfully upgrade to TLS 1.2 (read more here):
- Migrate to TLS 1.2, not 1.1, for the best protection
- Regularly patch and upgrade your TLS 1.2 software to protect against evolving threats
- Securely configure TLS
- Support secure TLS cipher suites and key sizes
- Disable support for cipher suites unnecessary for interoperability
- Read and use resources from the PCI Security Standards Council to make sure you’re fully compliant
From the same document, here’s an overview of where to get started:
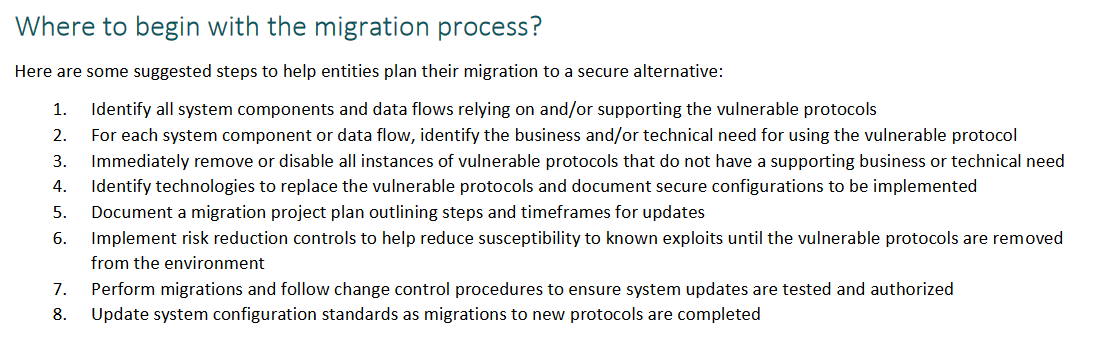
Source: https://www.pcisecuritystandards.org/documents/Migrating_from_SSL_and_Early_TLS_-v12.pdf
That’s it—those are the three steps you need to take to ace the TLS 1.2 upgrade. Once you make the switch, your company and your clients will be well guarded against outside attacks.

A commitment to security
The TLS 1.2 upgrade is only one in a long line of upgrades, patches, and changes made to better protect merchants and their customers. Although it’s the most secure protocol today, it will likely face vulnerabilities in the future. Information security is not a one-and-done deal—it’s an ongoing process that involves a firm commitment to staying up-to-date on current trends and constantly evaluating your environment to find better ways to secure it. Making the switch to TLS 1.2 is a small part of the always-changing security landscape, and we hope this article gives you the confidence you need to implement the TLS 1.2 upgrade.
 Is you business PCI compliant? Take this 1-min quiz to find out.
Is you business PCI compliant? Take this 1-min quiz to find out.