Blog > Storing Credit Card Information Safely in 2023: The Do’s and Don’ts
Storing Credit Card Information Safely in 2023: The Do’s and Don’ts
Storing credit card information requires due diligence from merchants. They have a responsibility to keep customer credit card data safe and create a secure environment. Unfortunately, not all merchants know the ins and outs of proper data storage protocol, and—even worse—not all care. However, insecure, non-compliant storage methods can lead to disastrous outcomes, like broken trust, steep fines, data breaches, and even the loss of a merchant account. To avoid these penalties, merchants can use third-party solutions to safely store credit card information and protect their customers—and their business—from harm.
Why storing credit card information safely matters
Merchants who take the time and effort to appropriately secure credit card information benefit from:
- Healthy, trusting relationships with customers
- A favorable reputation
- Peace of mind
On the other hand, merchants who fail to secure vulnerable information may experience:
- Broken relationships with customers
- A negative reputation
- Penalties and fines from their credit card processor, acquiring bank, and/or regulatory bodies
- The loss of their merchant account
- Lost time spent resolving data breaches and the resulting fallout
Checkout this quick video to learn the real cost of data breaches:
The worst ways to store credit card information
Unprotected on a local computer
The PANscan in 2020 found an astonishing 88% of merchants store unencrypted primary account numbers (PANs) on their networks. In 2022 Over 3,715,741 PANs were found on business networks. PANs are the 14-, 15-, or 16-digit numbers on the front of credit cards. Storing these numbers without any sort of protection is a flagrant breach of PCI compliance and could easily lead to a catastrophic data breach.
Common methods for storing credit card data on a local computer include spreadsheets (like Excel or Google Sheets), data saved in CRMs, and files saved to services like Google Drive or Dropbox. All of these examples are unsafe, non-compliant methods of storing vulnerable data.
Privileged access
Unfortunately, employees are often the source of data breaches. In a Data Breach Investigations Report by Verizon in 2023, 61% of breached organizations said the reason was due to privileged credential abuse. Essentially, an employee had greater access to data than they should’ve, and they exploited this weakness. To prevent privileged access attacks, merchants should regularly audit who has access to sensitive data and revoke any unnecessary privileges.
On paper
Believe it or not, some merchants store credit card information on paper. This kind of storage system can range from scribbling card numbers on sticky notes to keeping detailed records in organized files. Regardless, paper is one of the riskiest, most insecure methods of storing credit card info—and it’s also not in line with PCI compliance standards.
The number one risk associated with storing sensitive data on paper is theft. Both employees and bad actors steal paper records. Even if merchants keep their data in a locked filing cabinet, there’s always a risk of theft.
Why merchants don’t store credit card information properly
There are a few reasons why merchants may choose to store data improperly.
Convenience
Some merchants prioritize convenience over security. It’s convenient to store customer credit card data on an Excel spreadsheet on their desktop or jot down credit card numbers on sticky notes. When they need the information, it’s right there. However, this is obviously a dangerous and irresponsible way to handle sensitive information, and puts customer data at risk.
“No one will target me”
Another factor that leads merchants to store data incorrectly is the belief that bad actors won’t target their business. It’s hard to imagine that a hacker will home in on a mom-and-pop shop or a small business. But hackers actually prefer small businesses—they typically have lighter security and are relatively easy to steal from. Verizon’s 2023 report showed system intrusion, social engineering and basic web application attacks represents 92% of breaches for small businesses. Almost one third of data breaches found by Verizon’s 2020 Data Breach Investigations Report happened to small businesses, and a 2019 study found 63% of SMBs reported a data breach in the past year. Unfortunately, small businesses can’t ignore the very real threat of a data breach.
“Security solutions are too complicated”
Some merchants don’t want to bother upgrading their security. They have a system, and even if it’s flawed, they don’t want to invest the time needed to implement and learn a new system. The new technology may be complicated, clunky, or require more tech-savvy than the merchant possesses. But these fears are unfounded. The vast majority of security solutions that store credit card data are relatively easy to use. In many cases, they increase productivity and make credit card processing even more convenient.
“Security solutions are too expensive”
Similar to the objection above, some merchants simply don’t want to pay for better security. However, this is a cost-risk analysis that doesn’t pan out. It’s much, much more expensive to experience a data breach than to pay for the security solution that will prevent one. IBM’s 2022 Cost of a Data Breach Report found the average data breach costs $4.35 million. In addition, if a merchant experiences a data breach while failing to comply with PCI standards, they could face fines ranging from $5,000 to $500,000 and could even lose their merchant account. Any way you slice it, the cost of sticking with an old, insecure system far outweighs any security solution.
The best ways to store credit card information
Off-site storage
The best way to store credit card information is to outsource it to a third party wholly dedicated to protecting card data. These third parties store credit card information off-site on secure servers, removing the burden of storage from merchants entirely. Merchants don’t have to worry about securing their own networks according to outside standards, and their liability is greatly reduced.
There are a number of different solutions for storing credit card data, including secure vaults, services from payment processors, and payment gateways. Merchants should evaluate each solution on a number of factors, including:
- Level of security: How robust is the security solution?
- Level of need: What does the business actually need?
- Cost: Does the solution charge a monthly or annual cost? Does it actually save money?
- How the solution integrates with their current system: Can the security solution seamlessly integrate with other business software currently in use?
Below, we’ll get into three features merchants absolutely need from their credit card information storage solution.
Encryption
Encryption is a method of protecting data while it travels from one endpoint to another.
Regardless of how a card is processed—in person, over the phone, online, etc.—the transaction details have to travel back and forth between several different entities, like the credit card network and the acquiring bank. As this information moves, the sensitive data is translated into gibberish using a special key. Even if it’s intercepted while in transit, the information will be completely unintelligible. Only the validated recipients of the information will have the key needed to de-gibberify the data.
It’s important to note that encryption is not foolproof—it can be broken. That’s why it’s essential that merchants choose a security solution that uses both encryption and tokenization to safeguard data.
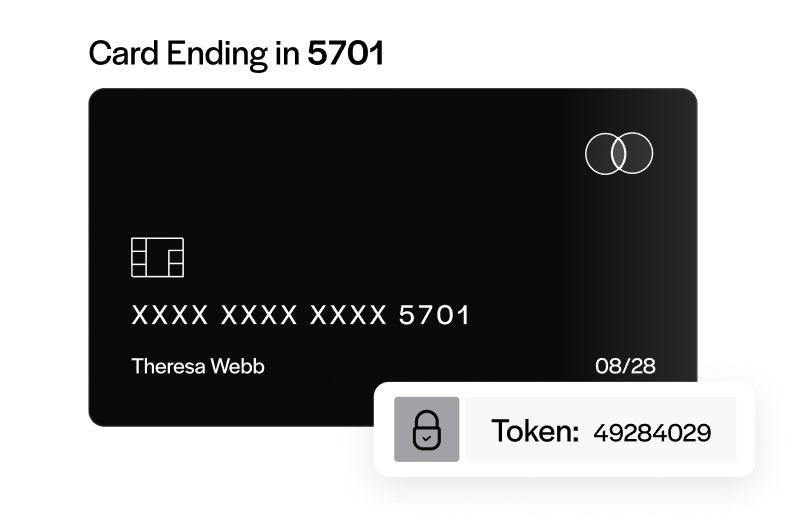
Tokenization
Tokenization is a method of protecting data while it’s in storage. Essentially, vulnerable data is replaced with a facsimile or a token. The real data is kept with the security solution, while the facsimile data is kept by the merchant.
Think of a locked vault with gold bars in it—the gold bars are safe up until the point someone breaks in. Tokenization is like replacing gold bars with paper facsimiles. Even if a thief breaches the vault, all they’ll find is completely worthless paper copies of the real thing.
The video below will help you understand how tokenization can secure your credit card information:
With tokenization, the merchant has the vault with the false paper gold bars, while the security solution maintains the vault with the real gold bars.
When the merchant needs to run a credit card payment, their system speaks with the security solution’s system. The security solution handles all the vulnerable data and sends it for authorization, so the merchant is never exposed to the original data.
Tokenized data is completely randomized and worthless. Unlike encryption, which translates each data point into a new one with a logical key, tokenized data bears no relationship to the original. If a thief gains access to tokenized data, there’s no way to revert it back to the original, vulnerable data. Only the security solution can swap out tokens for the real thing.
Paired with encryption, tokenization significantly reduces the chance of a harmful data breach.
PCI compliance
Every business that accepts, stores, or handles credit card data in any way must be PCI compliant. The PCI DSS, or data security standard, is a set of requirements that dictate how businesses should keep credit card data safe. They were created by the PCI Security Standards Council (SSC), which is made up of the five major credit card brands: American Express, Visa, Mastercard, Discover, and JCB.
The video below explains what PCI compliance is:
By maintaining PCI compliance, merchants adhere to the most advanced security guidelines in the industry. They protect their customers (and their business) from the risk of a harmful data breach. Every security solution merchants employ should be PCI compliant and recognized as a PCI DSS validated service provider.
In most cases, third-party security solutions alleviate the burden of PCI compliance on merchants by taking on the most difficult aspects of the protocol. While merchants are still responsible for ensuring their own environment is compliant, they can breathe a sigh of relief knowing their most vulnerable data is handled by a PCI-compliant solution.
Don’t forget hardware
Hardware like phones, terminals, and point of sale equipment are often weak points in a merchant’s secure environment. For example, a business that takes payments over the phone may have a bank of voicemails that include sensitive credit card information. Likewise, point of sale terminals are often the easiest access point for hackers to enter a network.
To solve this issue, merchants must include hardware in their security scope and work to protect it. For example, sensitive voicemails could be encrypted and password-protected, while merchants could choose PCI-approved point of sale terminals. EMV-equipped terminals also help cut down on fraud and provide an added layer of security to both merchants and customers.
Each business will have different needs and risks they must address, and it’s up to each merchant to determine what steps they need to take to secure their environment. Luckily, there are professionals like Qualified Security Assessors, or QSAs, who can help with this process.
Conclusion
Businesses that process credit card payments carry an important responsibility: their customers trust them to keep their sensitive data safe. While this endeavor isn’t always easy or straightforward, it’s necessary—and worth it. Fortunately, with the right tools, support, and knowledge, merchants can store credit card information safely and responsibly.