Blog > The Ultimate PCI Compliance Guide | Why it’s Essential + 10 Expert Tips
The Ultimate PCI Compliance Guide | Why it’s Essential + 10 Expert Tips
While payment security looks a little different for each merchant, it continues to remain a top priority across all industries. To help with this, businesses look to PCI compliance standards for guidance. Although these standards offer a lot of direction to better protect cardholder data, they are not foolproof against all cybersecurity attacks.
To meet evolving compliance standards and better prepare for growing cyber threats, we brought in 10 industry experts to help you build the strongest infrastructure possible.
What is PCI compliance?
PCI (Payment Card Industry) compliance is a fancy way of saying your business is following proper security measures to successfully accept, process, and store credit card payments. PCI compliance is not legally required but is mandatory in certain cases.
The Payment Card Industry Data Security Standard (PCI DSS) defines these security requirements. The PCI Security Standards Council (PCI SSC) — established by Visa, American Express, Discover, Mastercard, and JCB International credit card providers in 2006 — is responsible for upholding these standards, ensuring merchants meet them, and managing data security worldwide.
Check out this video below to learn more about PCI compliance.
PCI compliance: Levels, assessments, and requirements
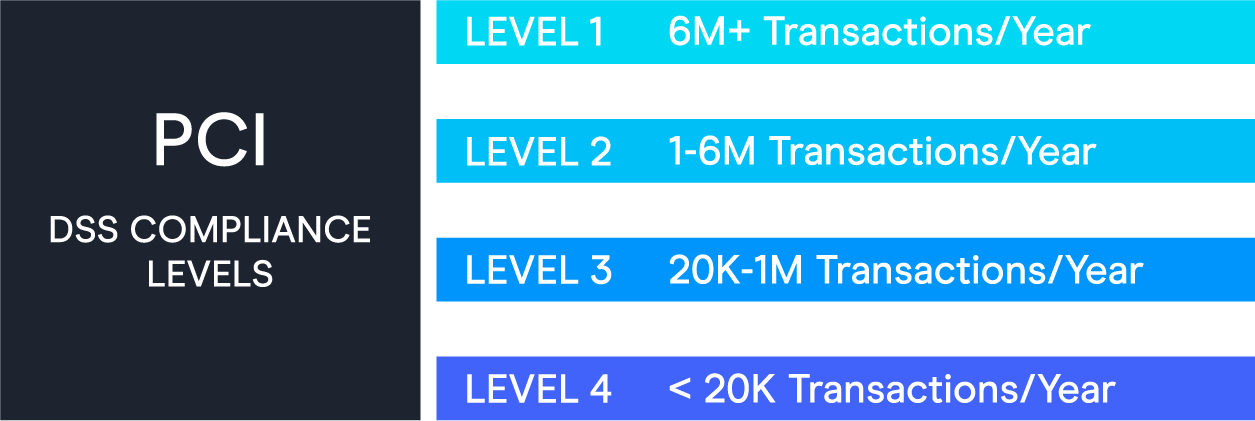
PCI levels are typically determined by merchants’ annual transactions and business size:
- Level 1: Merchants who process over six million transactions per year and service providers that process over 300,000 credit card transactions annually. (Typically large businesses.)
- Level 2: Merchants who process between one and six million transactions per year and service providers who process fewer than 300,000 transactions annually. (Typically mid-to-large-sized businesses.)
- Level 3: Merchants who process between 20,000 and one million transactions per year. (Typically small-to-mid-sized businesses.)
- Level 4: Merchants who process fewer than 20,000 transactions per year. (Typically small businesses.)
PCI validation assessments
A merchant’s PCI compliance level determines its annual and quarterly validation requirements. Depending on your level, here are some of the validation forms you may have to complete:
- Report on Compliance (ROC): Completed annually by a Qualified Security Assessor (QSA) to analyze an organization’s overall policies, procedures, and payment security.
- Attestation of Compliance (AOC): Sent to the acquiring bank to confirm compliance.
- Self-Assessment Questionnaire (PCI SAQ): Internal analysis to analyze if your business meets compliance. There are nine different assessments to choose from depending on how a merchant processes, manages and stores cardholder information.
- Quarterly vulnerability scans from Approved Scanning Vendors (ASV): Certify PCI compliance.
- PCI penetration testing: Used to verify a merchant’s cardholder protection and test security features for any risk or vulnerability.
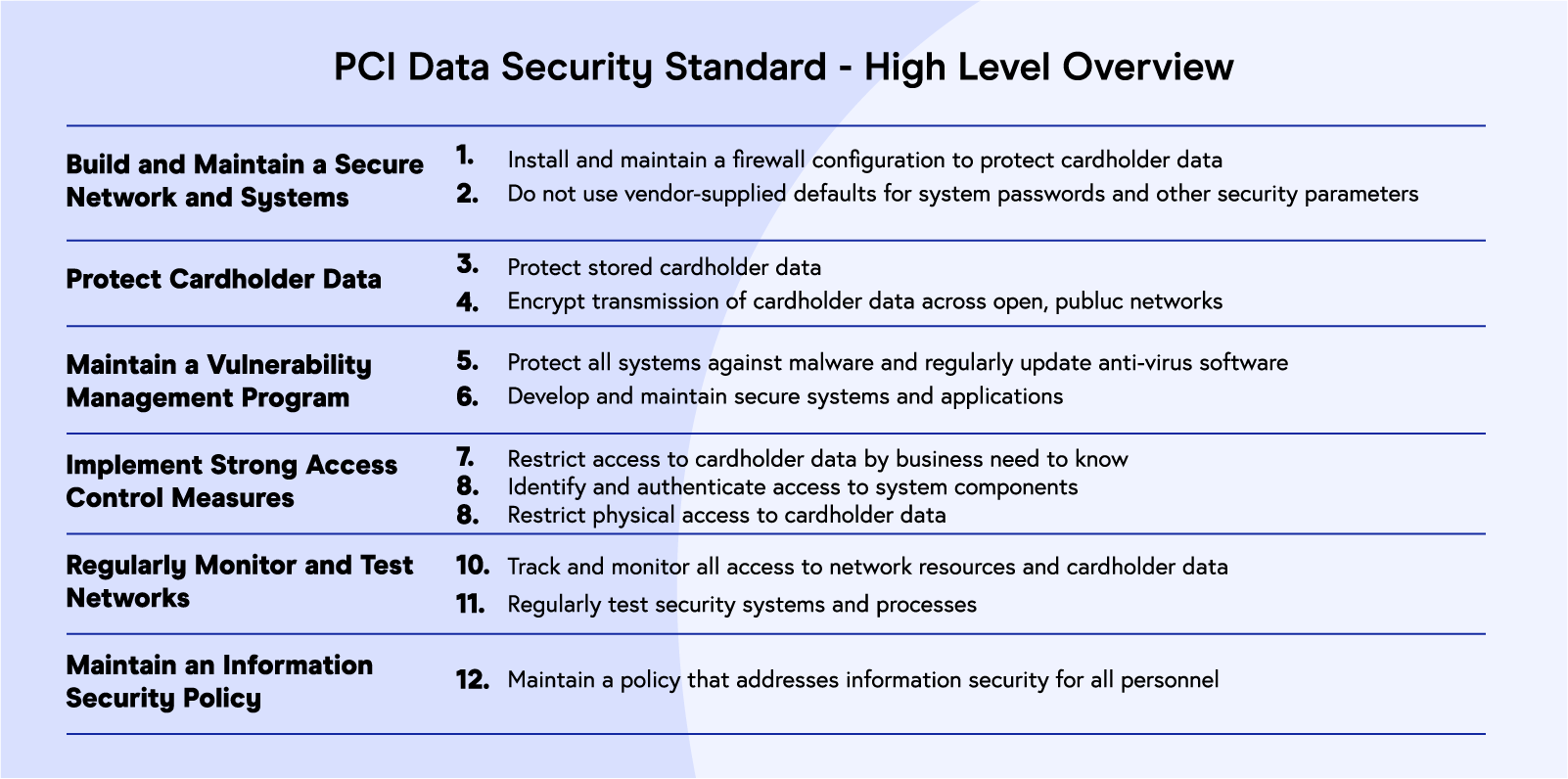
PCI DSS requirements
The PCI Security Standards Council provides merchants with a general list of security standards to follow to become PCI compliant:
 In addition to these 12 security standards, each compliance level has separate requirements merchants must complete:
In addition to these 12 security standards, each compliance level has separate requirements merchants must complete:
Level 1 merchants are required to provide:
- A Report on Compliance (ROC) completed by a Qualified Security Assessor (QSA) or Internal Security Assessor
- Quarterly scans by an Approved Scanning Vendor (ASV)
- An Attestation of Compliance (AOC) completed by a QSA
Level 2 merchants are required to provide:
- Self-Assessment Questionnaire (SAQ) completed by the merchant
- Quarterly scans completed by an Approved Scanning Vendor (ASV)
- An AOC completed by a QSA
- Sometimes an additional PCI scan
Level 3 merchants are required to provide:
- An SAQ completed by the merchant
- Quarterly scans completed by an ASV
- An AOC completed by a QSA
Level 4 merchants are required to provide:
- An SAQ completed by the merchant
- Quarterly scans completed by an ASV
PCI compliance benefits: A surefire way to limit breaches & save your business
“PCI Compliance is a widely accepted and expected information security standard. It gives your brand much-needed credibility and certifies your ability to handle card data and transactions. To the layman, it gives an assurance that their card details will be handled securely.”

Bram Jansen
Chief Editor at vpnAlert
While PCI compliance offers the obvious benefit of enhanced security, it can provide additional, sometimes unexpected advantages to your business.
Some of the top benefits of PCI compliance include:
- Lower risk of breaches
- Improved customer experience
- Enhanced brand reputation
- Increased operational efficiency
Lower risk of breaches
Since the purpose of the PCI DSS is to improve payment security, it would make sense that PCI compliance would also decrease the likelihood of breaches, fines, and lawsuits.
This decrease occurs because merchants create a more secure IT infrastructure that protects cardholder information through solutions like firewalls, encryption, tokenization, and more. By reducing these risks, you’re also reducing the potential for future fines (from acquiring banks, governments, etc.) and lawsuits (from retailers, credit card processors, customers, etc.).
Learn more about the risks of payment data breaches in this podcast below.
Improved customer experience
Merchants should prioritize their customers and take the necessary steps to make their experience the best it can be. If customers don’t trust your site, they probably won’t purchase from you.
A PwC report shows 87% of consumers say they’ll take their business elsewhere if they don’t trust a company to handle their data responsibly. By maintaining compliance, you’re putting the security of your customer first and providing a safer shopping experience. In turn, this will promote more confidence and trust to purchase.
Enhanced brand reputation
Customer experience and trust directly relate to brand reputation. By improving customer experience and trust through compliance, customers’ perception of your business will increase too.
This positive impact can influence customers to make return purchases, spread the word about your business and its products, and leave positive reviews, all of which can impact the growth of your business.
Increased operational efficiency
“PCI DSS compliance can offer operational efficiency by mapping the controls to other regulatory and security compliance frameworks that your business is obligated to adhere to and be audited against. Too often I find that controls are written in a vacuum and not designed with all applicable organization compliance needs. Whether PCI DSS is the first compliance framework your organization is implementing, or you’re adding it to an existing compliance program, designing controls with mapping in mind can lead to greater operational efficiency.”

Adam Brennick
Compliance Professional
After implementing the necessary PCI compliance protocols and software, businesses can improve their operational efficiency by using the extra time and resources that would’ve been spent on handling preventable security breaches to tackle high-priority tasks. Merchants can also use their compliance to meet other security regulations and standards.
Compliance requirements like penetration testing and vulnerability scans allow merchants to fulfill additional security standards such as the SOC 2 (Service Organization Control), ISO 27001 (International Organization for Standardization), and other global regulations.
How to become PCI compliant and avoid thousands of dollars in fines

“You can’t secure what you don’t know about. Know your environment, what data you have, where that data exists, and who has access to it. Then, minimize your attack surface. The cardholder data environment (CDE) needs to be segmented off from other areas of your network. It becomes much easier to be compliant with the PCI DSS when the CDE is walled off. Reduce your compliance scope and you’ll have an easier job being compliant.”

After your business has identified its PCI level and the applicable standards and validation requirements, your team can work together to better secure payment data and become PCI compliant.
The Security Standards Council (SSC) simplifies the process of becoming PCI compliant into three steps:
- Assess: Review cardholder data, assets, and business operations to identify any vulnerabilities or risks.
- Repair: Actively work to reduce risks and vulnerabilities and eliminate excess cardholder data.
- Report: Compile and submit the required information to acquiring banks and card companies.
To further help businesses become compliant, the PCI SSC has compiled a prioritized list for businesses to follow. Once these steps have been taken, your business can undergo a PCI self-assessment to make sure all data and security measures have been properly implemented. Merchants can also complete a vulnerability scan to double-check their security.
Costs of PCI compliance
PCI compliance costs vary based on many factors of your business. These costs can increase or decrease depending on:
- Business size and number of annual transactions
- Type of business and industry
- Level of security already put in place (or lack thereof)
- Whether or not the acquiring bank helps front some of the costs
- Company morale and employees’ willingness to adapt and learn security measures
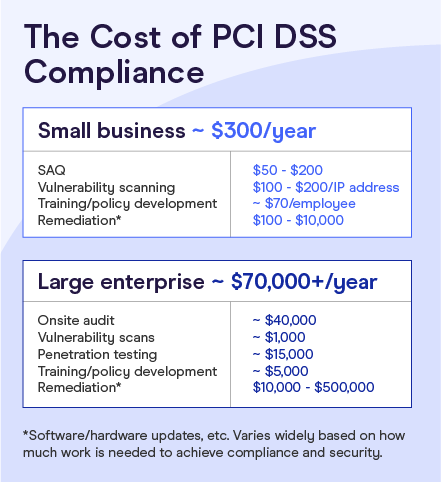
SecurityMetrics estimates PCI compliance costs to average around $300 annually for small businesses and $70,000 annually for large businesses. These cost differences fluctuate so dramatically because of the various assessment requirements and levels of compliance.
Penalties of non-compliance
“I think being compliant is enough to save money. If any breaches were to happen, you will be in a lot more trouble and paying so much more than you would now to mitigate it.”

Ethan Taub
CEO at Goalry
The threat of the non-compliance penalties your business can face greatly outweighs the cost of being PCI compliant. While the PCI SSC doesn’t enforce these non-compliance penalties, the five major credit card brands — Visa, Mastercard, Amex, Discover, JCB International — do.
A merchant’s acquiring bank is responsible for keeping them PCI compliant through an annual Self-Assessment Questionnaire (SAQ) and Report on Compliance (ROC). If the bank and its merchant fail to uphold PCI compliance, they are both liable to fines and penalties levied by the major credit card companies.
If a data breach occurs, the major credit card branches will determine if a merchant is upholding PCI DSS compliance and to what extent. Fines ranging anywhere from $5,000 to $100,000 per month can be placed on a business until full compliance is reached. Banks can and most likely will fine their merchants using additional fees or service charges.
Merchants who choose to not comply are subject to repeat fines. They also open themselves up to negligence lawsuits from banks, customers, card processing companies, and more.
How to improve PCI compliance and secure a foolproof infrastructure
“PCI compliance needs to be an ongoing initiative, not something a business only looks at once a year when they send in their Self-Assessment Questionnaire (SAQ) or every three years right before an audit.”

To improve PCI compliance, merchants must monitor many moving parts, like current events, new security technology, updated compliance standards, and changing demands for online payments.
Merchants can take the following additional actions to improve PCI compliance to build sustainable PCI compliance programs and secure cardholder data:
Compile a comprehensive inventory list (vendors, equipment, digital tools, etc.)
Knowing the ins and outs of your business and its assets can help you fix any gaps in security and eliminate outdated tools that no longer serve your organization. This auditing can also help merchants save more money by finding services and software that are all-in-one solutions.
Test your network systems regularly to ensure they’re working properly
Running regular assessments lets you test your systems, networks, and protocols to find any weaknesses or vulnerabilities that need to be addressed. It’s not enough to simply add new features without any follow-up — you must constantly monitor and manage your security infrastructure to make sure it’s running smoothly.
Use strong passwords, data encryptions, and security policies
Implementing unique passwords, encryptions, and security policies are vital to your business. Hackers continue to get smarter, and using the same passwords, outdated encryptions, and old-school security will leave your business more vulnerable to these threats.
Put a heavy focus on overall cybersecurity and employee training surrounding it
Cybersecurity best practices and routine employee training will serve as invaluable tools for merchants. Using the right services and software only gets you so far, especially if you don’t have the right people managing them. Human error is a huge internal threat to your business, so it’s important to conduct regular training for all employees, including C-level executives.
Honestly assess your business’s internal risk and security structure
Merchants need to be honest about what threats lie inside their own walls. Every business has its own threats and vulnerabilities. Identifying and addressing these issues will not only save you money but also save your reputation in the long run. Running regular audits in all areas of your business will help mitigate these risks.
Preparing for PCI DSS v4.0 to customize your security for your needs

With the new PCI DSS v4.0 expected to roll out in mid-2021, industries will be expected to update their security to stay compliant.
According to the Security Council, PCI DSS v4.0 focuses on three objectives:
- Continue providing a solid foundation for payment security as systems evolve
- Promote security as a continuous process
- Allow businesses more flexibility to use various methods and technologies to maintain compliance
While there are no major changes coming to the 12 security standards, these are a few updates to four PCI standards to address the recent influx in payment security threats:
- Authentication: Multi-factor authentication can help secure businesses and make them more compliant by adding extra identification steps before accessing important cardholder information.
- Encryption: This updated standard will help direct businesses to trusted networks with strong data encryption to combat the growing threat of malicious code and malware.
- Monitoring: New requirements will ensure merchants regularly monitor their infrastructure and stay up to date, so they can safely use new technology.
- Critical control testing: Businesses may need to test critical controls more frequently and add additional protocols from the Designated Entities Supplemental Validation requirements. (In the past, these requirements typically only applied to compromised businesses.)
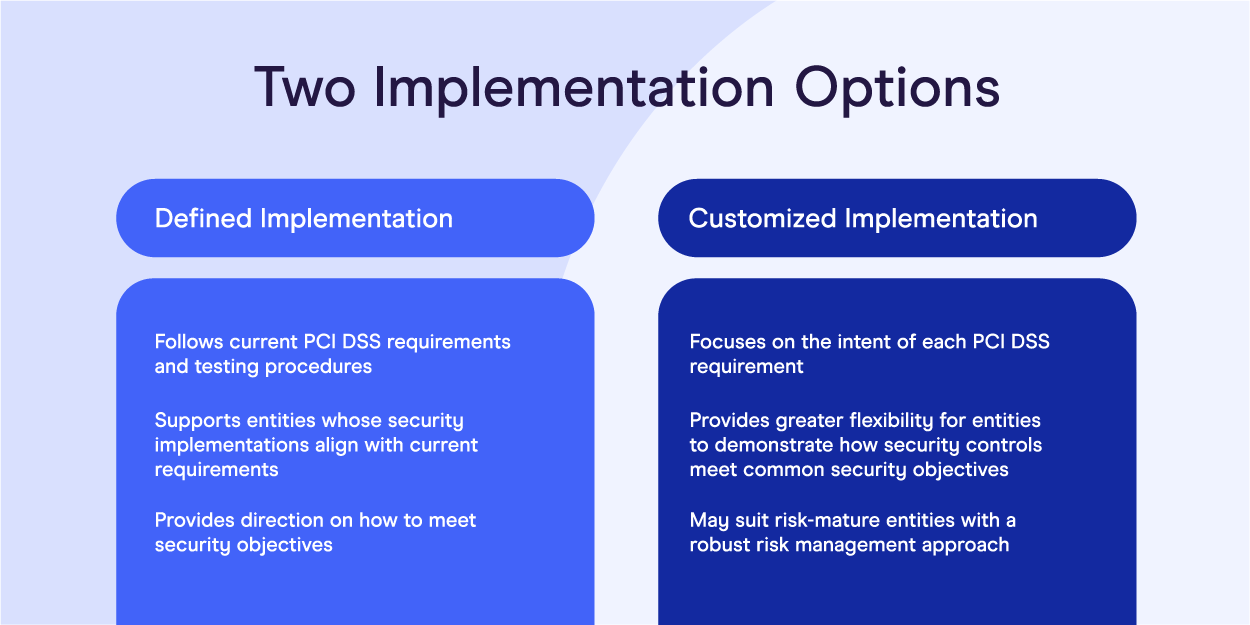
Defined vs. customized implementation
These new PCI DSS 4.0 differs from previous updates by giving merchants more flexibility. Merchants can either follow the written requirements to a tee (defined implementation) or choose the security features or methods best suited for their business (customized implementation).
Defined implementation
The defined approach simply means your business follows current PCI DSS requirements and procedures precisely as they are published.
Customized implementation
The new customized approach means your business focuses on the intent of each PCI DSS requirement and security. With this approach, merchants can choose how to secure their businesses (methods and technologies), but they must show how they meet compliance requirements.
To validate using the customized approach, SecurityRisk Advisors provides details about the information expected from your organization:
- The who, what, where, when, and how of the controls
- Proof the controls meet the security intent
- Evidence of how controls are maintained and effectiveness
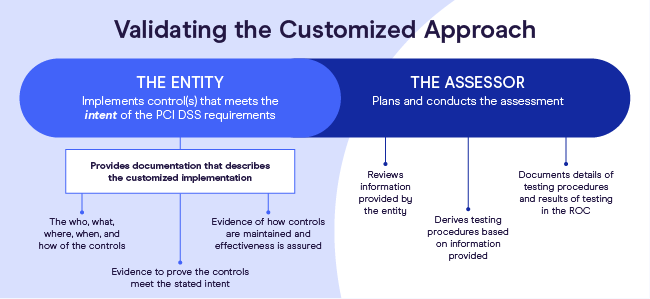
After receiving these details, a Qualified Security Assessor (QSA) assesses the information provided, tests the controls, and compiles a Report on Compliance (ROC), which documents how these features operate and if they’re compliant.
Tips to prepare for PCI DSS v4.0
While implementing changes in your security controls can seem like a daunting task, many industries most likely unknowingly have updated their compliance due to the pandemic.
If for some reason your business hasn’t updated its cybersecurity or payment security features, here are some tips to help:
- Get rid of unnecessary data and sensitive data to avoid potential breaches
- Identify all highly sensitive data and add additional security protections
- Manage up-to-date network diagrams to see how they interact with protected data
- Meet with a QSA (not just for an assessment) for advice and review of new protocols
- Involve your PCI stakeholders to collaborate, address, and eliminate errors or threats
- Make sure all partners and third parties stay PCI compliant and update their systems
While merchants wait for the official 4.0 requirements to go live, they can start preparing by reviewing the recent updates from the PCI Security Council, which detail the new PCI Software Security Framework replacement, SPoC Security Standard, and more.
Payment security trends to grow your brand for the future

With payment security as a top priority for most merchants, many are putting their trust in evolving technologies and emerging trends to protect cardholder data and meet new PCI requirements.
According to Mordor Intelligence, the payment security market brought in $17.98 billion in 2020 and is expected to reach $42.91 billion by 2026. As COVID-19 continues to force industries fully remote, online payments and their security protocols have grown into a significant focus for most businesses.
One cybersecurity expert mentions three trends he’s noticed:
“Biometric verification: Biometric scanning for payment methods is now increasing because it’s easier, faster, and more secure. PIN codes and passwords are a thing of the past now.
Mobile wallets: A virtual wallet in your smartphone integrates with your credit or debit card and allows you to make payments through your mobile phone.
Contactless payments: Contactless payments suddenly gained importance because of COVID-19. It’s now expected to be one of the fastest-growing digital payment trends. You just need to hover your card over the payment device, and your payment will be made.”

Merchants should also consider other payment security trends, like:
- AI, machine learning, and cloud technology
- Open banking
AI, machine learning, and cloud technology
With continued advancements, artificial intelligence has made it easier for businesses to detect fraudulent activity almost instantly. Merchants and banks can add machine learning to their AI to easily compile more data for predictive analyses and learn from suspicious payment behavior.
The global payment gateway market is expected to grow by $23.45 billion between 2020 and 2024. This growth will largely be due to cloud technology, which allows merchants to streamline the digital payment process by accelerating transactions and collections. Cloud-based gateways also provide more security for cardholder data and reduce operational costs for businesses.
Open banking
Open banking is the use of API technology (apps) to allow customers to pay merchants via instant bank transfers. This allows for a faster and more secure payment processing to occur, with no cards or data present.
The open banking market is projected to reach $43.15 million by 2026. Open banking allows for banks to collaborate with fintech businesses and third parties to develop apps and services together, instead of competing against them. These applications allow customers to control their own data and pay merchants quicker.
With cyber attackers catching on to this popular trend, industries are increasing their use of safety features like authentication and authorization controls, transaction security, and more.
Security risks that could crush your business: How to identify, manage, and reduce them

In 2020, the U.S. held the highest total average data breach cost at $8.64 million, a $450,000 increase from 2019. Most of this influx can be attributed to the ongoing pandemic that’s forcing businesses online.
Even more concerning than the drastic increase in data breaches is the number of compliant businesses — or lack thereof. Only 27.9% of organizations were PCI compliant in 2019, a percentage that has continued to decrease over the years.
With cybersecurity threats at an all-time high, businesses have felt the pressure to address and reduce risks to improve their overall payment security. Now more than ever, it’s vital for merchants to honestly evaluate their infrastructures to tackle these threats.
To improve PCI compliance and payment security, merchants must first identify both external and internal threats that pose the greatest risk to their business.
Top threats to cyber and payment security
Since COVID-19, the FBI has reported a 300% increase in cybercrimes. With this increase, Cybersecurity Ventures projects cybercrime damages to reach $6 trillion in 2021. Therefore, businesses would be wise to learn about common threats and attacks to better prepare.
Some of the top threats to payment and cybersecurity include:
- Poor endpoint and patch management
- DoS/DDoS and IoT attacks
- Phishing
- Insider threats
Poor endpoint and patch management
“Unsecured network endpoints, such as customer Wi-Fi access points, provide easy access to hackers seeking to steal customer data. Also, access to the store’s website — data is often obtained using malware hiding in encrypted web traffic (HTTPS).”

Almi Dumi
CISO at eMazzanti Technologies
Poor endpoint and patch management open the door for malicious attacks on endpoint devices like laptops, smartphones, tablets, desktops, servers, etc. The lack of in-house firewalls and security features when working remotely has put these devices at a greater risk for breaches.
In Q3 of 2020, there was a 50% increase in the daily average of ransomware attacks. Endpoint security threats like ransomware target devices with poor patching to gain access to data, restrict users and system administrators from accessing files or networks, and then leverage this attack to demand payment from the business.
DoS/DDoS and IoT attacks
Both denial of service (DoS) and distributed denial of service (DDoS) attacks occur when an overflow of requests from fake IP addresses disrupt traffic to your server, network, or service, so you can’t respond to requests and your server fails. These attacks differ in that a DoS comes from one attacker and a DDoS uses multiple attackers to target one system.
Internet of Things (IoT) attacks rose by 35% in the first half of 2020 compared with the end of 2019. These threats are projected to continue increasing, as many are still working from home and shopping online on IoT devices. IoT attacks typically occur when hackers are near target devices.
Remote users accessing IoT devices lack the strength of corporate security walls, which gives hackers an opportunity to access important data like card information, passwords, and full control of networks.
Phishing
Phishing attacks have been in full swing since the pandemic began. According to Proofpoint’s 2021 State of the Phish Report, 75% of surveyed organizations faced successful and unsuccessful broad phishing attacks, and more than half paid ransoms to get their data back.
The most common types of phishing threats come in the form of emails, texts, calls, and even social media. Credit card information and login credentials are the most common objectives of these efforts.
Spear phishing attacks use a more personalized approach by targeting a specific person and using information about this person (typically found on social media) to gain access to data.
Insider threats
“The human factor is the biggest vulnerability of any organization. Ongoing training and awareness are key in mitigating the risks involved with human behavior and reducing the risk of errors which can compromise the security and privacy of personal data and damage an organization’s reputation.”

Insider attacks are predicted to make up 33% of breaches in 2021. With data moving to remote access via clouds, emails, network storage, public Wi-Fi, and more, there’s more opportunity for hackers. Mobile apps can also open the door to malicious activity through embedded malware.
While 95% of breaches are due to human error, there is also the risk of bad actors becoming trusted employees to capture sensitive IP data and payment information. Remote work has made it even easier for hackers to get hired without stepping foot in your office.
Additional threats
Additional cybersecurity and online payment threats include:
To learn more about common online payment threats like fraud involving account takeover, refunds, promotions, and more, eCommerce merchants can click here.
How to manage and reduce risks
“Since business risk is associated with vulnerabilities, the core of any mature Risk Management Program is an effective Vulnerability Management Program. The mission of a Vulnerability Management Program is to identify and mitigate vulnerabilities, lowering the overall risk to an acceptable level. This level is often referred to as an organization’s risk tolerance.”

Richard Anderson
Chief Security Officer at Century Business Solutions
After you have a better understanding of potential threats your business can face, you can use this information to improve your overall payment security and PCI compliance strategies.
Merchants should honestly assess their internal risks and vulnerabilities to produce a comprehensive plan to manage and reduce them.
A strong Risk Management Program evaluates the likelihood of various scenarios and how they may affect your business, then sets up an infrastructure to resolve them. These programs should also factor in the costs of various strategies, tools, and resources to see if they’re worth the spend.
Security solutions and services: The invaluable tools you need to outlast competitors
According to Juniper Research, merchants are estimated to lose $24 billion to online payment fraud by 2024. With eCommerce selling showing no sign of slowing, businesses are more susceptible to threats that aim to steal important data like cardholder information. Now more than ever, it’s crucial to improve your security.
While the PCI SSC provides steps for businesses to improve security, merchants should always look to new technology, tools, protocols, online trends, and more to combat growing threats and update security programs.
One expert offers his advice for merchants:
“Sign up with a cyber company to alert you of data breaches that you may be included in, and your information showing up on the dark web. Keep all your devices updated with the latest operating system patches and antivirus software; run scans often. NEVER click links in an email or download attachments. Train your employees on cybersecurity. Do not use the same passwords on multiple sites (no matter how tempting it might be). Always use long, complex, and random passwords. Have secured Wi-Fi.”

David Lukic
Cyber Security Consultant at IDStrong
Some additional solutions to enhance your cybersecurity and PCI compliance include:
- Encryption
- Tokenization
- Ransomware protection
- Internal fraud prevention
- Outsourcing third-party services
Encryption
An Unbound Tech 2019 survey found that 66% view encryption key management as a big or medium challenge. Nowadays, standard encryption by itself is not sufficient in securing your system.
If you aren’t already using end-to-end encryption or point-to-point encryption, you need to. Both are highly beneficial in protecting digital communication and payment data to help businesses remain PCI compliant.
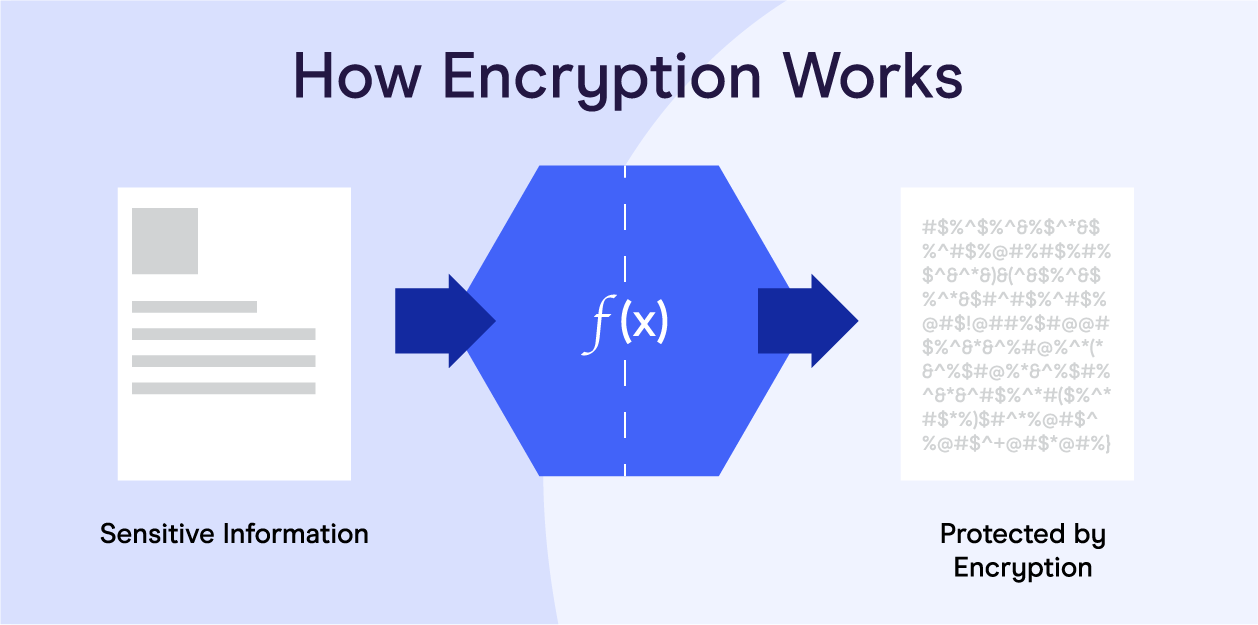
End-to-end encryption (E2EE) establishes secure and private communication between senders and recipients. E2EE is meant to prevent hackers or third parties from accessing any messages or files by not allowing any stored data to be decrypted on the server.
Point-to-point encryption (P2PE) was developed by the PCI SSC to protect payment data in transit and during card-present transactions. This encryption protects cardholder data from the moment it’s captured until it reaches its endpoint (solution provider or payment processor) to be decrypted. Merchants using contactless payments can use this encryption to better secure their systems and reduce PCI scope.
Merchants can also use other data encryption techniques like:
- Symmetric encryption: Gives the sender and receiver access to the same key, meaning both parties are responsible for safely securing the key.
- Asymmetric encryption: Uses public and private keys that pair with each other. The public key is available to anyone and the private key is only meant for intended recipients to decipher.
- Hashing: Generates unique encryption for each message and is only used to verify data, not for deciphering.
- Homomorphic encryption: Keeps encrypted data intact and unexposed while being processed, manipulated, or stored in the cloud. This allows employees and third parties to use this data without knowing or accessing the decrypted messaging.
Like all security, encryption is not foolproof. Merchants should use trustworthy software for the best protection and PCI compliance.
Tokenization
Tokenization replaces sensitive data (card or bank information) with nonsensitive data in the form of tokens using the same format. This method makes it nearly impossible for anyone other than the payment processor to read the token and helps businesses keep PCI compliance.
Cloud-based tokenization can also be a great tool to protect merchants against evolving cyber threats by capturing card data and storing it outside of internal systems. This can save you money on on-premise tokenization costs, reduce your scope, and advance security efforts.
Ransomware protection
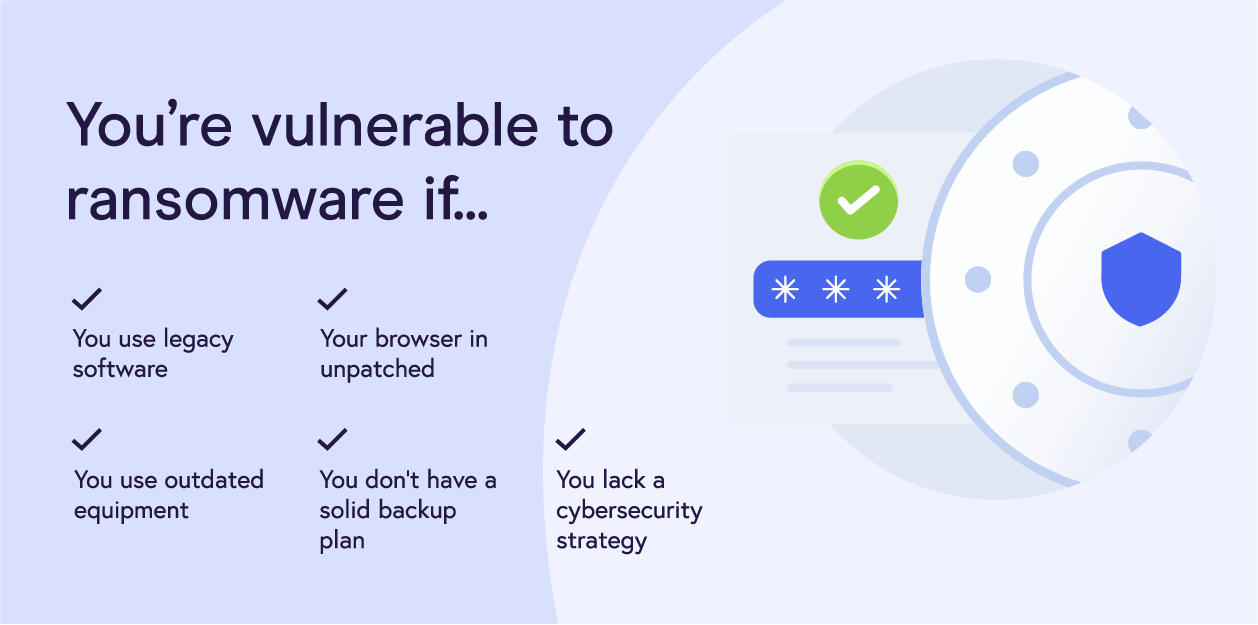
With global ransomware damages estimated to reach $20 billion and attacks projected to occur every 11 seconds in 2021, merchants need to do their best to protect their data by implementing the necessary infrastructure.
In addition to the countless ransomware detection and prevention tools to choose from, businesses can implement other solutions and strategies:
- Run local and in-cloud automated system backups
- Use zero trust security solutions to provide uniform security across all devices, especially while remote; 40% surveyed are actively looking into zero trust technologies
- Install email gateway software to protect employees from malicious email threats
- Use physical and/or virtual network segmentation to control traffic flow, protect IoT devices and cardholder data, and reduce PCI compliance costs and scope
- Employ endpoint detection and response (EDR) security for better endpoint monitoring, data analysis, and threat response
Internal fraud prevention
Since insider threats can cause a lot of damage to your business, building strong internal fraud prevention and detection programs can be highly beneficial for your team and customers’ data.
To implement a strong infrastructure within your organization, the first step is continuous employee training. With the world of eCommerce constantly evolving, your cybersecurity protocols should be adjusted and updated accordingly.
There are several strategies to help your team maintain a cohesive security plan and eliminate unnecessary human error:
- Educate employees about the latest cyber and payment security threats, schemes, remote access procedures, and best practices
- Limit access to sensitive data and cardholder information to high-level employees (management) or need-to-know parties only; create unique access IDs for them
- Put together strong cybersecurity and PCI compliance policies and taskforces
- Collaborate with your C-suite executives and department managers on new security measures to implement across departments and conduct regular training
- Decommission outdated security tools and technologies
In addition to employee training, merchants can improve their infrastructure using tools like:
- Fraud detection APIs: Fully automated process, real-time data, and a more personalized approach
- Remote desktop protocol (RDP): Safely access network resources, databases, and applications
- Multi-factor authentication (MFA): Multiple authentications required to reduce automated attacks, bulk phishing, and data breaches.
- Data loss prevention program (DLP): Better data security and compliance readiness.
- Hardware and software firewalls: Maintain firewalls to prevent unauthorized parties from accessing sensitive data.
- Virtual private network (VPN): Boost privacy when using Wi-Fi, encrypt communications, and protect private information (passwords, cardholder data).
- Risk management software: Helps to maintain compliance, predict behavior, streamline reporting and analytics, and more.
For additional internal fraud prevention tools security like digital footprint analysis, data enrichment, and more, eCommerce merchants can click here.
Outsourcing third-party services
With 70% of breaches coming from on-premise systems, merchants can look to trusted third-party services to delegate security tasks. Although outsourcing services may sound like a bigger threat to PCI compliance, using third-party actors allocates sensitive data to different networks for more protection.
It’s never a good idea to store all your data on one network, server, or in one location. Plus, third parties can help businesses be more productive, efficient, and focused on high-priority tasks.
Merchants should look to trustworthy, PCI-compliant third-party services to improve their security. Some of these outsourced services include:
- Payment gateways: Helps manage, process, and collect payments safely
- Cloud computing services or distributed cloud computing: Helps with virtualized IT, accessible analytics, scalability, increased business performance, etc.
- Managed detection and response (MDR) solutions: Offers advanced threat detection and analysis, threat hunting, human monitoring, etc.
- Intrusion Detection Systems (IDS): 24/7 monitoring of network traffic to detect unusual behavior or policy violations
While these services offer many benefits to merchants, if they’re not properly managed, they can be susceptible to future breaches and non-compliance consequences. Regardless of which services you outsource, it’s important to safely use third-party services to protect sensitive data and cardholder account information.
Additional solutions and services
There are countless solutions and services to better secure your system, protect customer payment accounts, and stay compliant. Here are some additional ones to choose from:
- Breach and attack simulation (BAS) tools
- Phishing protection solutions
- SQL security tools
- Spam filters
- Anti-malware software
- Vulnerability scanning and pen test software to run regular assessments
- PCI compliance software
Remember, these solutions and cybersecurity protocols aren’t one-size-fits-all. With differences in business size, industry, transaction volume, and more, each merchant needs to conduct a thorough evaluation to identify their unique security needs and PCI expectations.
15 payment security statistics you need to know

Now that you understand the ins and outs of PCI compliance, here are 15 statistics to consider when updating your PCI and security plans:
- Healthcare has the highest industry average data breach cost at $7.13 million (IBM).
- Over 40% of privacy compliance technology is projected to rely on AI by 2023 (Gartner).
- Only 27.9% of organizations reached full PCI compliance in 2019 (Verizon 2020 PSR).
- 53% of companies have over 1,000 sensitive files open to every employee (Varonis).
- Credential theft, social attacks (i.e., phishing, malicious emails), and errors cause 67% of breaches or more; 58% of breaches involved personal data (Verizon 2020 DBIR).
- 83% of respondents plan to assess and purchase new automation tools to streamline their risk management and compliance operations in 2021 (Hyperproof).
- The U.S. is the most targeted country for ransomware — attacks increased by 98% in Q3 2020 (Checkpoint).
- Connected IoT devices are projected to reach 75 billion by 2025 (Statista).
- 70% of consumers believe businesses aren’t doing enough to secure their personal information (Arcserve 2020 Data Attack Surface Report).
- 49% of security leaders say their top priority is improving the protection of sensitive data (2020 IDG Security Priorities Study).
- Due to COVID-19, 49% of consumers are shopping online whenever possible (VISA Back to Business Study).
- The average breached organization is not compliant with 57% of PCI DSS requirements (SecurityMetrics).
- A centralized data governance program saved businesses an average of $3.01 million (Ponemon Institute).
- Online payment fraud is estimated to cost eCommerce over $25 billion annually by 2024; payment gateways are vital in ensuring security requirements are implemented to scale (Juniper Research).
- 77.4% of respondents say their IT and security teams have a negative relationship; 55% say driving collaboration between them will be a top priority over the next year (VMware 2020 Cybersecurity Outlook Report).
Conclusion
As eCommerce and digitalization trends continue to advance, PCI compliance will remain an invaluable and necessary asset for merchants. Ensuring your business has a comprehensive cybersecurity plan and updated payment security protocols will be key in preventing attacks, saving money, and achieving long-term success.
Summary
- What is PCI compliance?
- PCI compliance benefits: A surefire way to limit breaches & save your business
- How to become PCI compliant and avoid thousands of dollars in fines
- How to improve PCI compliance and secure a foolproof infrastructure
- Preparing for PCI DSS v4.0 to customize your security for your needs
- Payment security trends to grow your brand for the future
- Security risks that could crush your business: How to identify, manage, and reduce them
- Security solutions and services: The invaluable tools you need to outlast competitors
- 15 payment security statistics you need to know
- Conclusion
 Is you business PCI compliant? Take this 1-min quiz to find out.
Is you business PCI compliant? Take this 1-min quiz to find out. 